Alright, now you should have a two big files, one is the firmware itself, the other one is the contents of the eMMC (basically the installed default apps). Like so (for northern Europe device model):
| Size | Filename |
|---|
| 1.6G | DFL61_HARMATTAN_30.2012.07-1.NORTHERNEUROPE_EMMC_NORTHERNEUROPE.bin |
| 1.2G | DFL61_HARMATTAN_30.2012.07-1_PR_LEGACY_001-OEM1-958_ARM.bin |
Next turn off the device and make sure it is not plugged into your computer. Then start the flasher:
$ sudo flasher -f \
-F DFL61_HARMATTAN_30.2012.07-1_PR_LEGACY_001-OEM1-958_ARM.bin \
-F DFL61_HARMATTAN_30.2012.07-1.NORTHERNEUROPE_EMMC_NORTHERNEUROPE.bin \
--erase-user-data=secure
Note: For getting rid of the security code (that we don't know) the --erase-user-data=secure option is important, don't forget it.
Flasher should now output something like this:
flasher 3.12.1 (Oct 5 2011) Harmattan
WARNING: This tool is intended for professional use only. Using it may result
in permanently damaging your device or losing the warranty.
Suitable USB interface (bootloader/phonet) not found, waiting...
Flasher is now waiting for the device, so plug in the USB cable now. Flasher should now respond with:
USB device found at bus 001, device address 016.
Device identifier: xxx923xxx468xxx (SN: N/A)
Found device RM-696, hardware revision 1507
NOLO version 2.3.6
Version of 'sw-release': DFL61_HARMATTAN_30.2012.07-1_PR_001
Sending ape-algo image (7096 kB)...
100% (7096 of 7096 kB, avg. 11826 kB/s)
Suitable USB interface (phonet) not found, waiting...
USB device found at bus 001, device address 017.
Device identifier: xxx923xxx468xxx (SN: N/A)
Raw data transfer EP found at EP2.
Ping attempt 1 (250 ms)
Server application: 1.7.2
Found product RM-696 rev. 1507
Server implements softupd protocol version 1.8
Battery level 89 %, continuing.
Erasing, this may take a while.
It is now erasing the EMMC and as it says, can take a while. Took around 5-10 minutes for me. The white led should blink while it is doing it.
After a successful erase operation, the flash should respond with this:
Erase done.
Image SW version DFL61_HARMATTAN_30.2012.07-1_PR_001
Image moslo not present
Image tar skipped
Image config skipped
Battery level 93 %, continuing.
And then continue to the real flashing part, something like this (sizes will vary with different image files):
image [state progress transfer flash speed]
---------------------------------------------------------------------
[x] cert-sw [finished 100 % 1 / 1 kB NA ]
[x] cmt-2nd [finished 100 % 95 / 95 kB NA ]
[x] cmt-algo [finished 100 % 789 / 789 kB NA ]
[x] cmt-mcusw [finished 100 % 6050 / 6050 kB 3231 kB/s]
[x] xloader [finished 100 % 23 / 23 kB NA ]
[x] secondary [finished 100 % 94 / 94 kB NA ]
[x] kernel [finished 100 % 2714 / 2714 kB 7 kB/s]
[x] rootfs [finished 100 % 1163796 / 1163796 kB 10600 kB/s]
[x] mmc [finished 100 % 1627169 / 1627169 kB 16524 kB/s]
Updating SW release
Success
Unplug the USB cable and your N9 should now reboot into a fresh install !
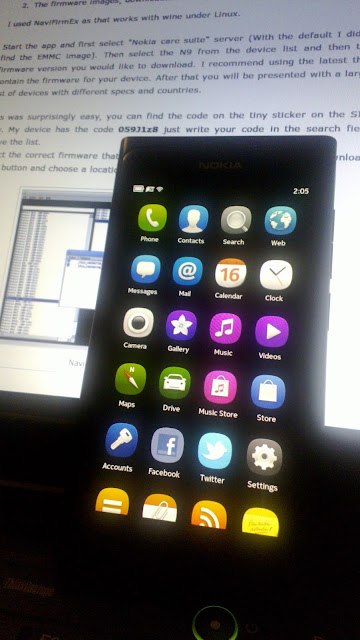 |
| Fresh N9 |
Enjoy.

